This week only: 23% Off + a 1-on-1 call with our experts. ⏰ : 1d 13h 25m 28s
Essentials: Crypto Security in 2025
Picture this: you log in expecting to see your portfolio at all-time highs. The numbers should be green and climbing, confirming years of dedication and discipline. You hit refresh once. Twice. But the balance doesn't change. It stares back at you: zero.

For a moment you convince yourself it's a glitch. Then the cold hard truth starts to set in. The funds aren't coming back. You've just been scammed. What took years to build has vanished in a single mistake.
This nightmare is playing out across the industry with growing frequency. Security is no longer optional; it is the only safeguard against irreversible loss. What follows is a breakdown of how these attacks unfold and the steps you can take to protect yourself.
Here's how...
Disclaimer: This is not financial or investment advice. You are responsible for any capital-related decisions you make, and only you are accountable for the results.
Introduction: Op-Sec as First Principle
The scope of the problem is unprecedented. Chainalysis data shows that more than $2.17 billion has already been stolen in the first half of 2025. The largest share came from North Korea's Lazarus Group, whose 1.5 billion dollar breach of Bybit set a new record for crypto theft. Beyond service-level attacks, personal wallets now account for nearly a quarter of all stolen funds. This shift highlights a harsh reality: individuals, no matter how experienced, are now primary targets.Events from this past week underscored the risks. On September 8, an NPM maintainer account was hijacked, and malicious updates were pushed to several popular open-source packages that collectively seen billions of downloads each week. The injected code was designed to intercept crypto transactions and replace wallet addresses with attacker-controlled lookalikes. Ledger's CTO, Charles Guillemet, publicly raised the alarm after detecting the issue and urged users to pause sensitive activity until the threat was contained. Thankfully, the financial damage was limited, with only $159 stolen. But the incident served as a stark reminder of how fragile the ecosystem is when trusted supply chains can be compromised at the source.
Security is the foundation of long-term survival in this market. The threat surface spans social manipulation, technical exploits, centralized custody risks, and even physical coercion. Only a combination of awareness and disciplined prevention can create true resilience.
Social Engineering: Exploiting Trust
The most common exploits in crypto are not technical but psychological. Platforms like Discord, Telegram, and X are built for frictionless communication, but that same convenience makes them prime channels for exploitation. Attackers lean on urgency and perceived credibility to overwhelm judgment. Moderators, influencers, and even official project accounts become high-value targets for impersonation or compromise.Impersonation Scams
A familiar pattern plays out across Discord communities. A user posts a support question, and within minutes a "helper" appears in their DMs. The account mimics an admin's name and profile picture, offering a solution through a link that looks like the project's site. Once the victim enters their seed phrase, the wallet is finished. Sweeper bots drain any funds that enter it.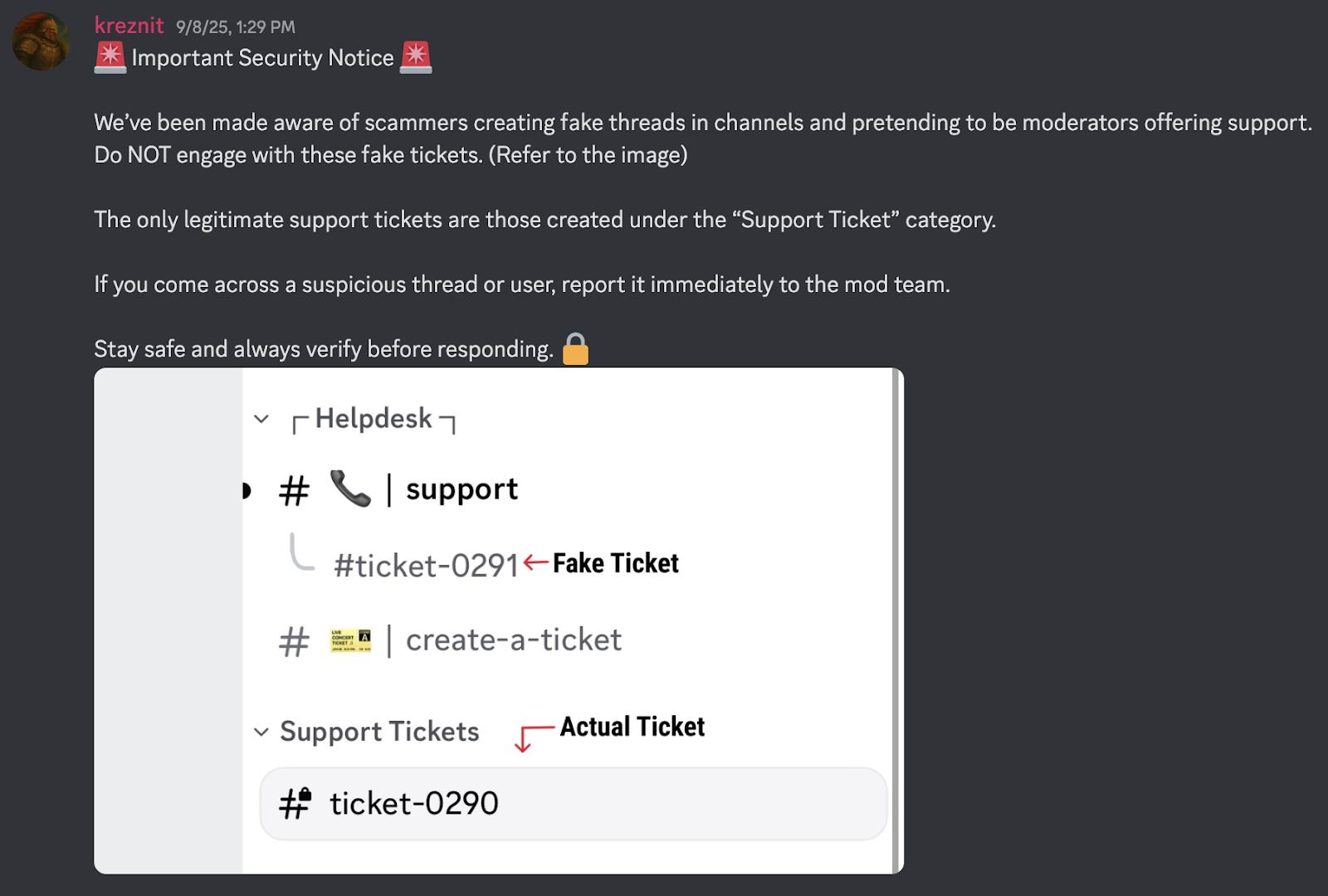
Some attackers go further by fabricating entire support ticket systems. Fake "support" threads are created inside channels to lure victims, complete with ticket numbers that resemble legitimate ones. Users believe they are speaking to project staff, when in fact they are engaging directly with the attacker.
Moderator Hijacks
Not all scams come from impostors. Increasingly, attackers compromise the accounts of real moderators, turning trusted community figures into vectors of exploitation. This often begins with OAuth2 phishing links disguised as verification or airdrop requirements. The links request extensive Discord permissions through malicious redirects. Approving the request hands over control of the account itself.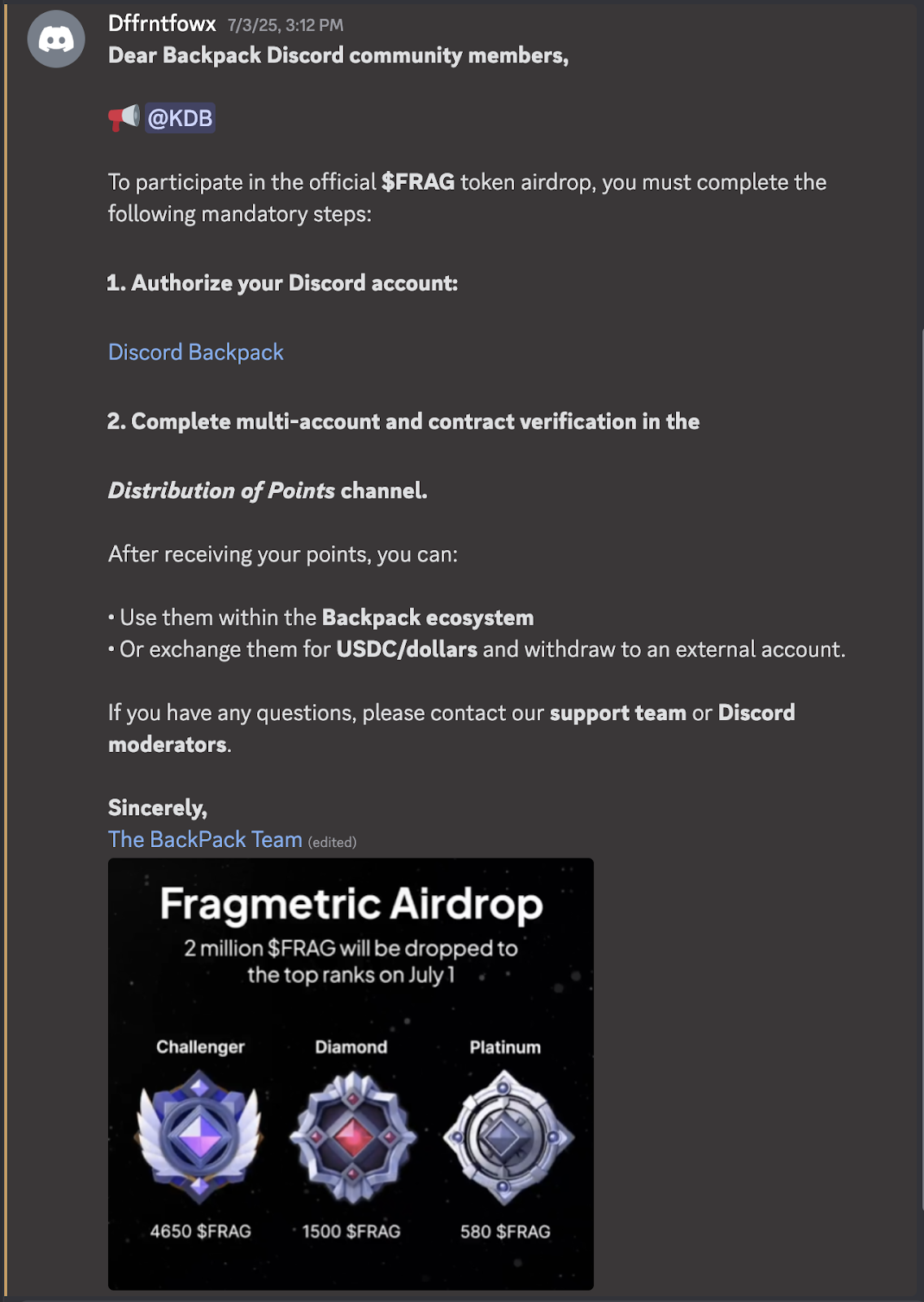
One example tied to a mid-tier project used a fake "Discord Backpack" authorization link. Hovering over the URL revealed a malicious redirect that, if approved, would have given attackers access to the victim's Discord account. With that access, they could DM users, post announcements, and distribute fraudulent links at scale.
Community-Level Compromises
This method was deployed at a much larger scale in June 2022, when Yuga Labs' social manager had his verified account hijacked. Attackers used it to post an "exclusive BAYC x Otherside Giveaway" directly inside the official channels. Eager holders connected wallets, only to unknowingly approve drainer contracts. In minutes, NFTs from Bored Ape Yacht Club, Mutant Apes, and Otherside were stolen and consolidated into attacker-controlled wallets. The lesson is clear: community security is only as strong as its least cautious administrator.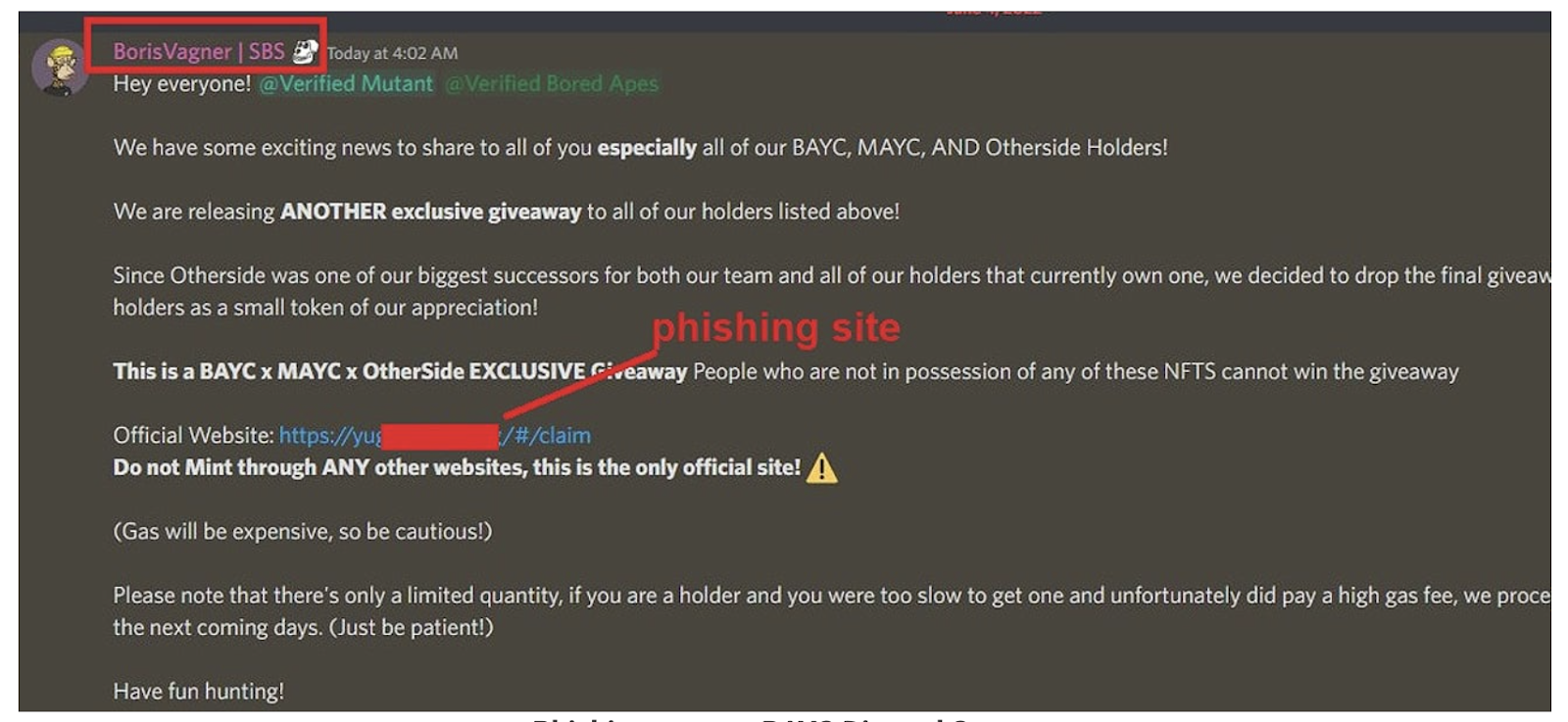
Phishing Campaigns
Phishing campaigns have also grown more sophisticated. After the collapse of FTX, creditors were targeted with emails that looked identical to official claim notices. The links redirected to drainer sites. Victims, already desperate to recover losses, were induced to compromise themselves. A simple but effective defense is to inspect sender addresses carefully. Attackers rely on slight variations in spelling or domain names to bypass cursory checks. A claim email that looks authentic may originate from a completely unrelated domain.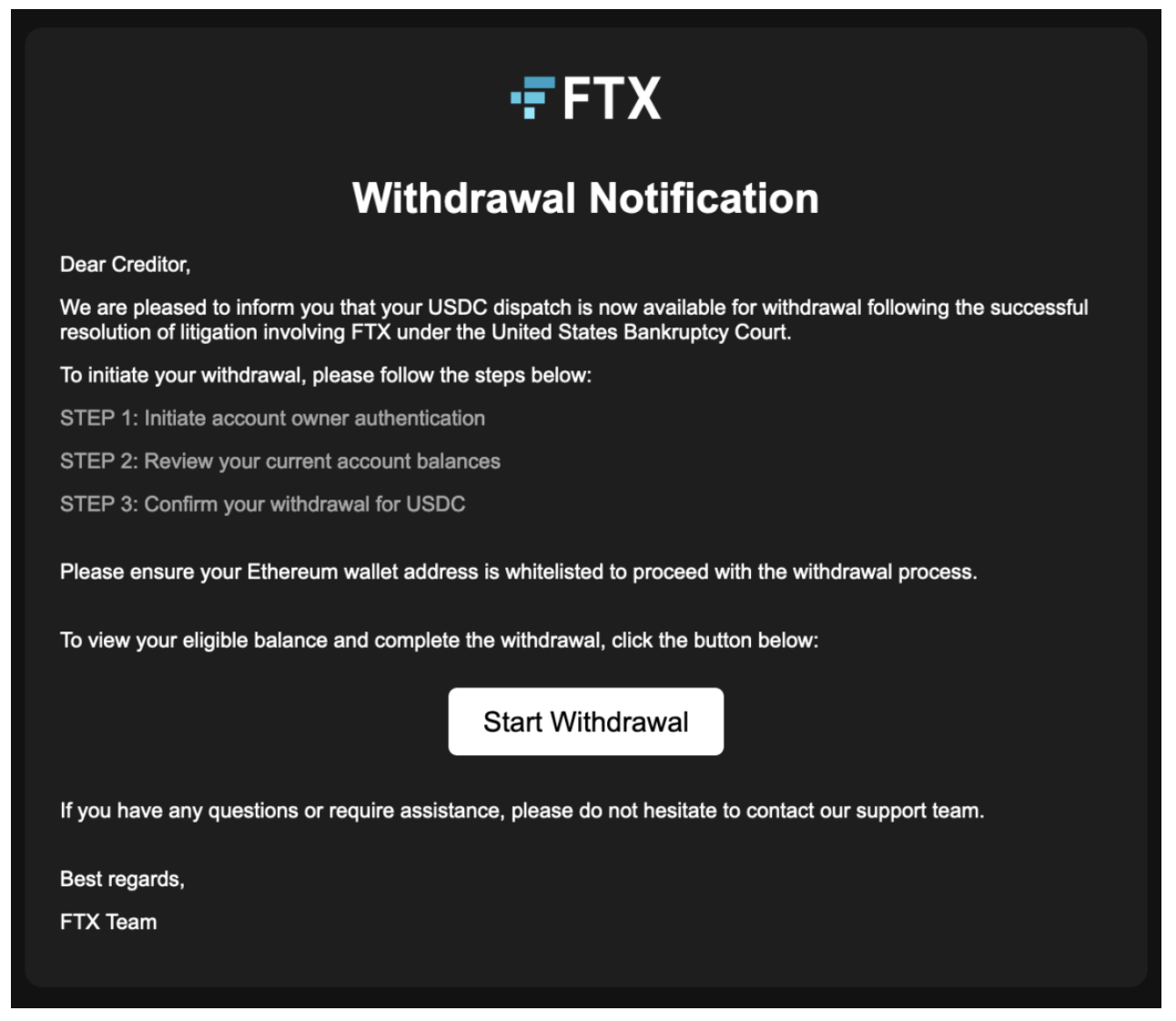
The recent compromise of an NPM maintainer illustrates the same principle. The developer was deceived by a 2FA-themed phishing email, which led to malicious updates being published across widely used open-source libraries. These packages were modified to intercept transactions and replace wallet addresses with attacker-controlled lookalikes. The incident was contained quickly, but it showed how social engineering can pierce even technical supply chains by targeting individuals rather than code.
Weaponized Calls and Meetings
Zoom has also become a vector for compromise. In one incident, attackers hijacked the credentials of a community manager at a DeFi project and used them to host an official-looking call. The event appeared legitimate, with branding and structure designed to mimic a standard community update. During the session, participants were directed to download what was described as a "mandatory upgrade." In reality, the file contained malware that harvested sensitive information, likely including private keys and wallet access. Several participants later discovered their wallets drained, demonstrating how trusted communication channels can be weaponized to deliver malicious software directly to users.Broadcast-Scale Deception
At a larger scale, social engineering becomes mass exploitation. Vitalik Buterin's X account was hacked in 2023 and used to promote a fraudulent NFT drop that netted nearly $700,000. Reports later confirmed that the compromise was the result of a SIM swap, where attackers convinced a telecom provider to reassign his phone number to a SIM card they controlled. With that access they bypassed SMS-based two-factor authentication and took over the account. The prevention lesson is clear: SMS is not secure. Users must switch to app-based or hardware-based authentication methods, and whenever possible, lock their SIM with a carrier-level PIN.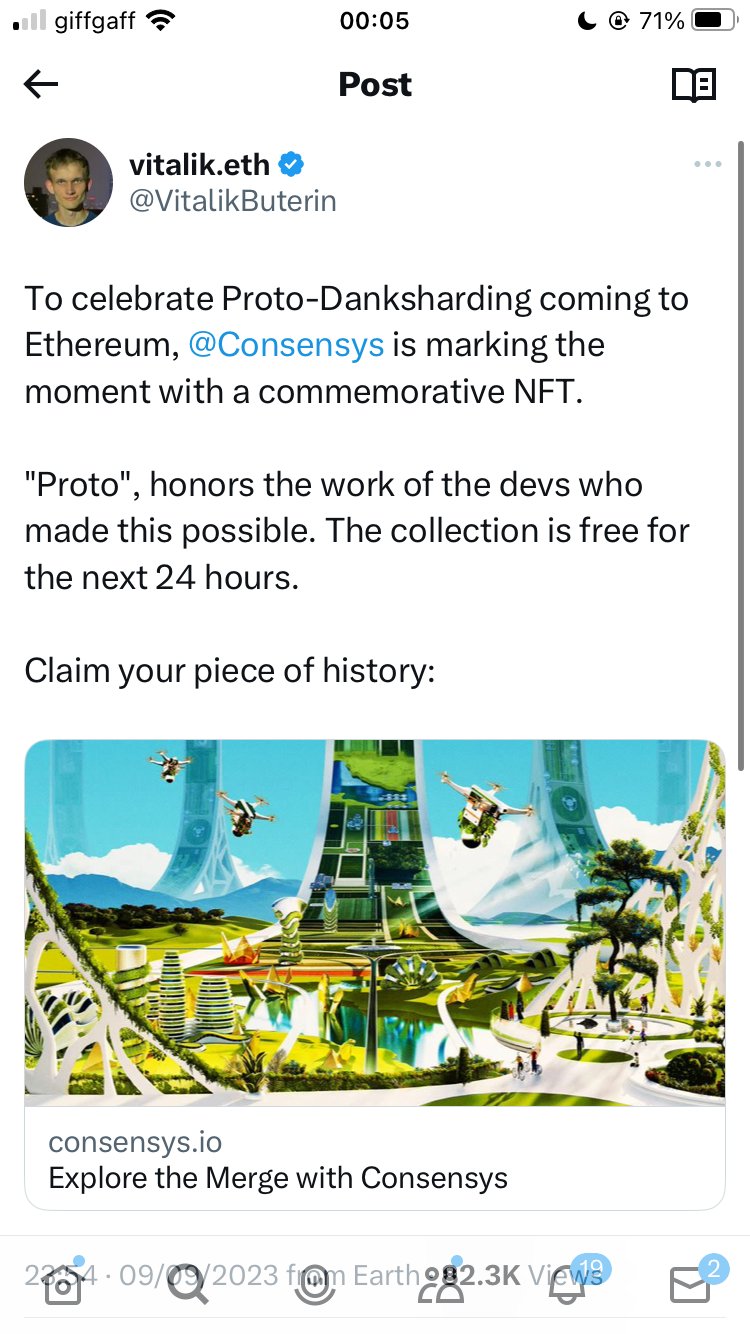
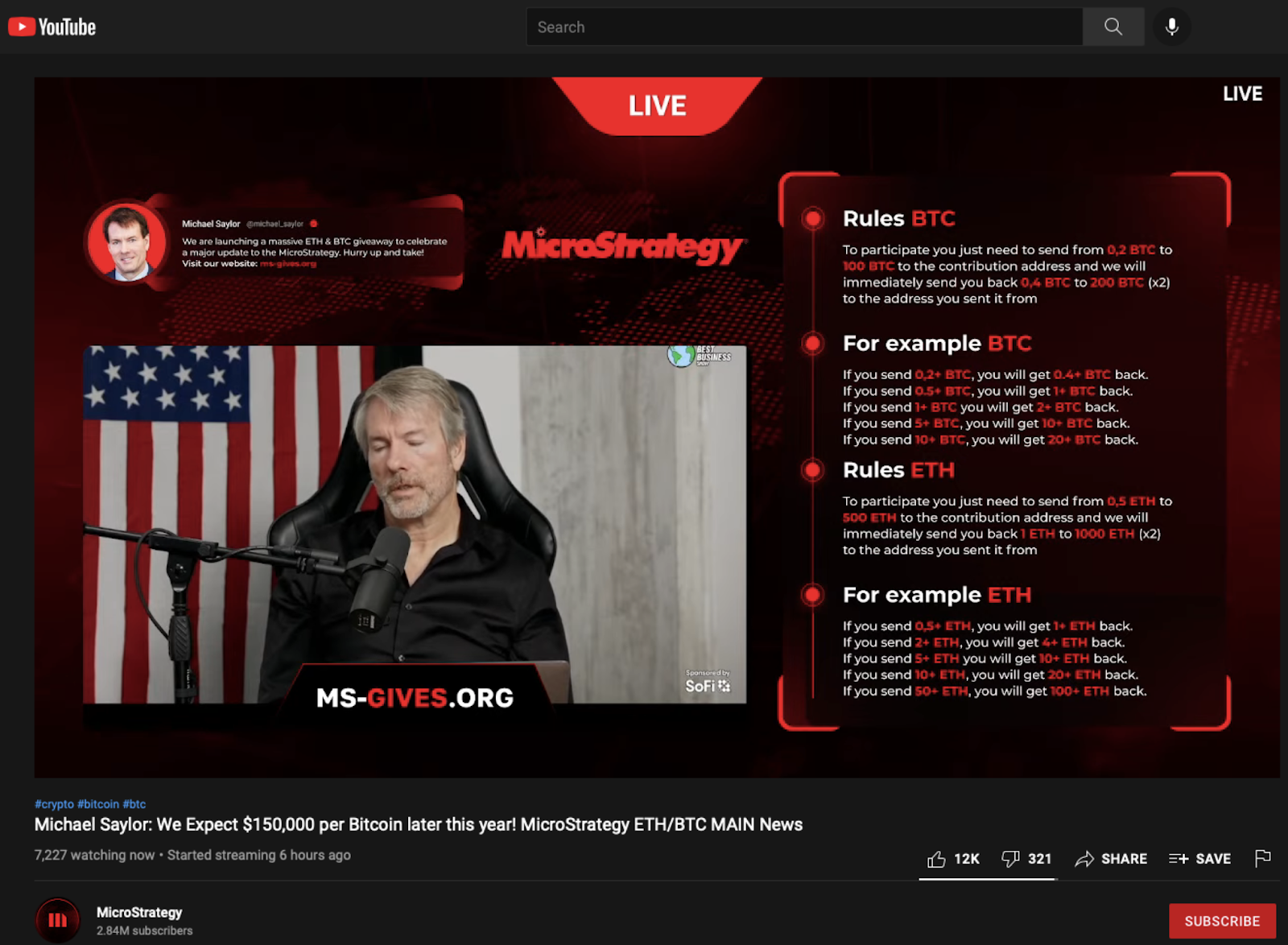
YouTube has emerged as an even larger battlefield. Scammers compromise high-subscriber channels and repurpose them into "crypto giveaway" streams. The formula is simple and effective. Recycled interviews with figures like Michael Saylor and Elon Musk are broadcast under the guise of breaking news. Viewers are told they can "double" their Bitcoin, Ethereum, or other tokens by sending funds to an address. Once funds are sent, they cannot be recovered.
Prevention
Mitigating social engineering begins with structural changes. Discord and Telegram allow DMs from strangers by default; disabling them eliminates one of the most common entry points. Users should verify moderator usernames carefully, but even verified accounts can be compromised. A standing rule should be that no moderator or admin will ever request a seed phrase or private key. Authorization prompts must be treated with the same caution as on-chain transactions, since OAuth2 hijacks can be just as dangerous.
The broader defense is cultural. Communities must reframe how authority is perceived. Moderators and influencers should not be seen as unquestionable sources of truth. Every request should be met with skepticism, and every link should be cross-checked against official sources. The failure to reset these cultural defaults is what allows social engineering to remain the most persistent attack surface in crypto.
Equally important is exercising common sense. Trust your instincts. If something feels suspicious, it probably is. Never rush into clicking a link or approving a transaction under pressure. Take the extra moment to confirm details, and if you are in doubt, ask for a second opinion from trusted peers or the Cryptonary community. Often the difference between safety and disaster is simply slowing down.
Technical Exploits: Automation at Protocol Speed
While social engineering manipulates trust, technical exploits attack the invisible infrastructure of crypto. These operations are precise, automated, and once triggered, nearly impossible to reverse. The sophistication lies not in deceiving people, but in silently rewriting the very rules that govern how users, wallets, and protocols interact.Malicious dApps and Transaction Hijacking
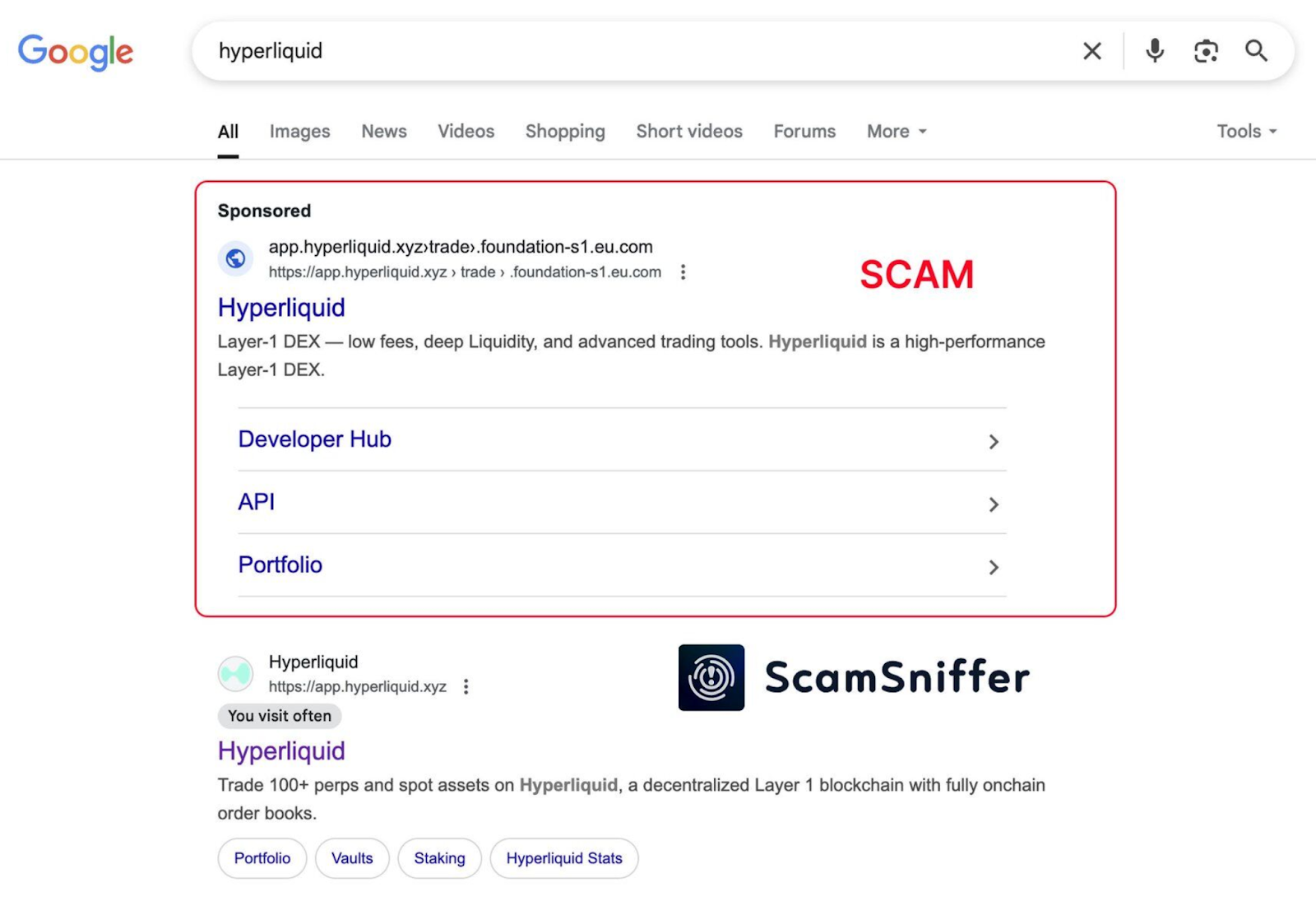
Fraudulent dApps often present themselves as legitimate interfaces, prompting users to sign transactions that appear routine but conceal dangerous permissions. Calls such as setApprovalForAll or transferFrom grant attackers the ability to empty wallets long after the initial interaction. Google's ad system amplifies the risk. Sponsored results frequently place phishing domains above genuine sites. A search for "Hyperliquid" can return a malicious clone at the very top of the page, complete with branding and design elements that are indistinguishable from the real product.
Fake Apps and App Store Abuse
Attackers have turned mobile app stores into highly effective traps. Counterfeit versions of wallets and exchanges are published in both iOS and Android marketplaces, often with inflated review counts and misleading descriptions to appear legitimate.One of the most dangerous tactics is prompting new users to "import" their wallet upon setup. Victims are asked to enter their seed phrase, believing they are restoring an existing account. In reality, the seed is transmitted directly to attacker servers, giving them full control of the wallet.
A recent example was a fake Hyperliquid Wallet app that surfaced in official app stores with convincing branding and screenshots. Users who entered their seed phrase had their funds stolen instantly. App store delays in identifying and removing these listings only worsen the damage. By the time takedowns occur, losses can already run into the millions.

Address Poisoning
Address poisoning is deceptively simple but effective. Attackers send dust transactions from vanity addresses designed to resemble trusted counterparties. Later, when victims copy a previous transaction from their history, they may unknowingly select the attacker's address. Funds are misdirected without raising immediate suspicion, often only discovered once it is far too late.
Clipboard Hijackers
On-device malware remains one of the most dangerous but underestimated attack vectors. Clipboard hijackers monitor copied data and silently replace legitimate wallet addresses with attacker-controlled strings. This can be triggered by something as simple as opening a disguised file. In one case from Q2 2025, a treasury administrator opened a PDF that secretly installed a remote access trojan (RAT). The malware altered clipboard contents in the background, and a subsequent $10 million transfer was redirected in full. Since the change is nearly invisible to the user, clipboard hijackers remain one of the hardest threats to catch without dedicated protection.Sweeper Bots
Once a seed phrase is exposed, the wallet is effectively finished. Sweeper bots are automated programs that monitor the blockchain mempool for activity tied to compromised wallets. The moment new funds arrive, the bot submits a higher-gas transaction that front-runs the victim's transaction and drains the wallet instantly. Attempts to "rescue" the wallet by sending in extra funds only accelerate the loss.Prevention
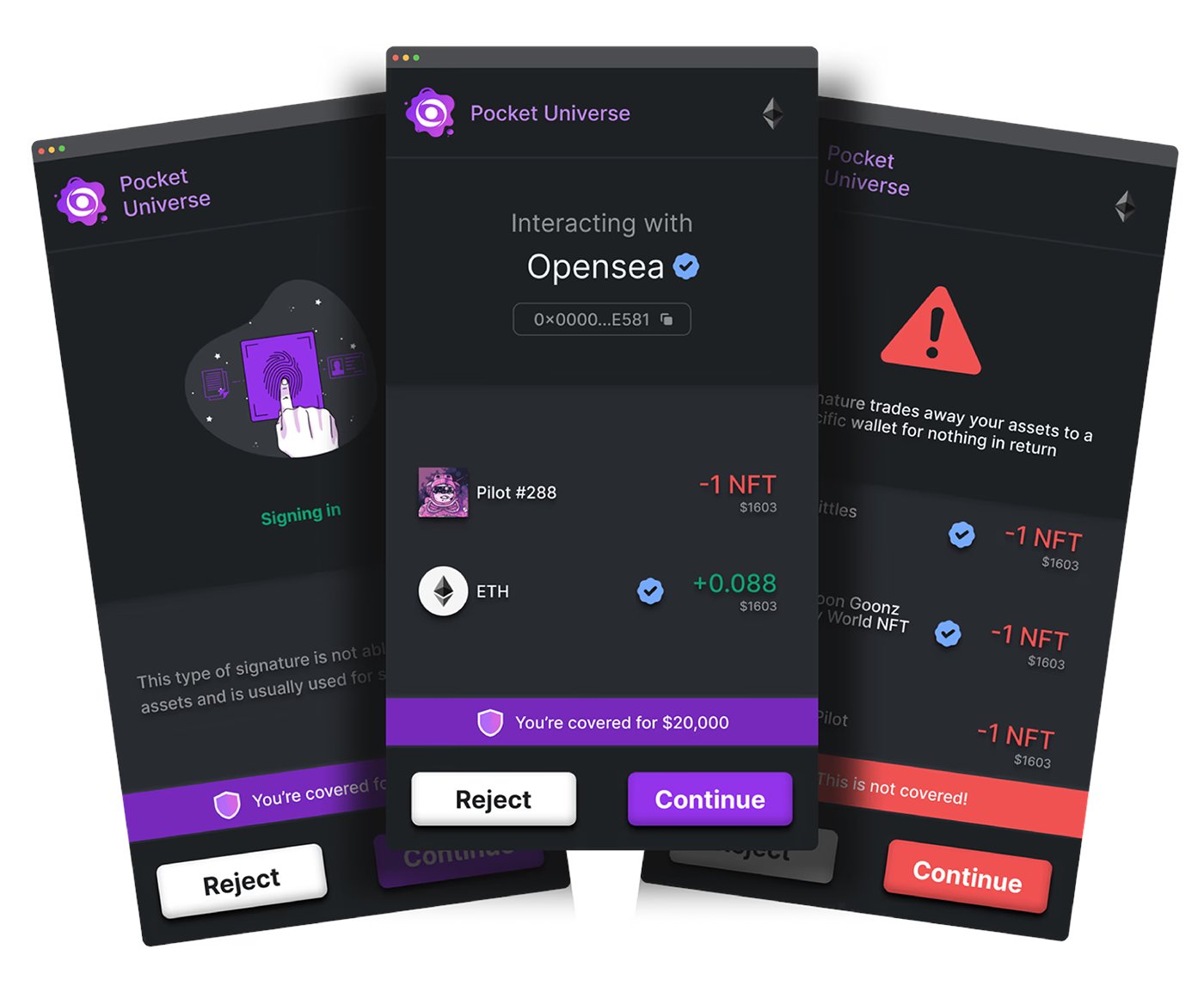
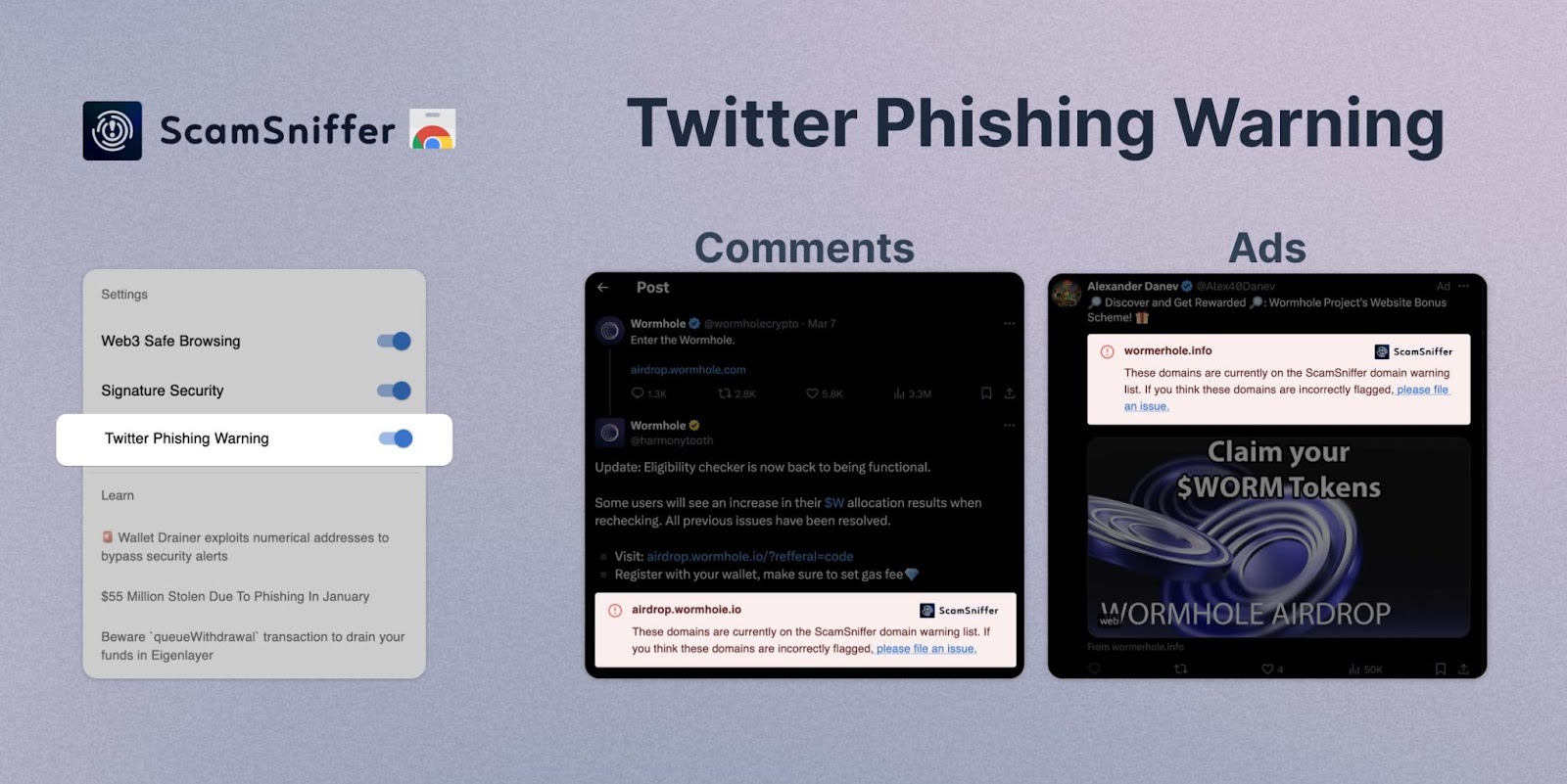
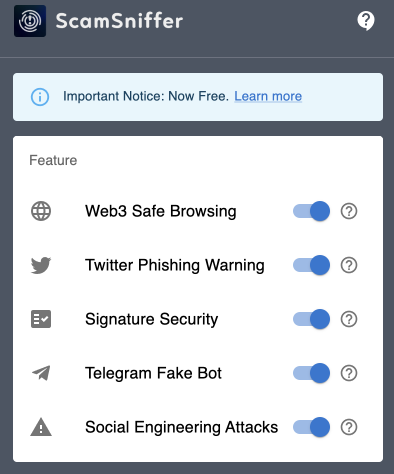
Defending against technical exploits requires layered safeguards rather than reliance on any single measure. Every transaction should be simulated before signing. Platforms like Pocket Universe and ScamSniffer provide previews that flag hidden approvals, malicious functions, or suspicious domains before a signature is confirmed. Both tools also extend beyond wallets, offering protection on social channels: Twitter phishing detection is now a core feature, intercepting malicious links before they reach the browser.
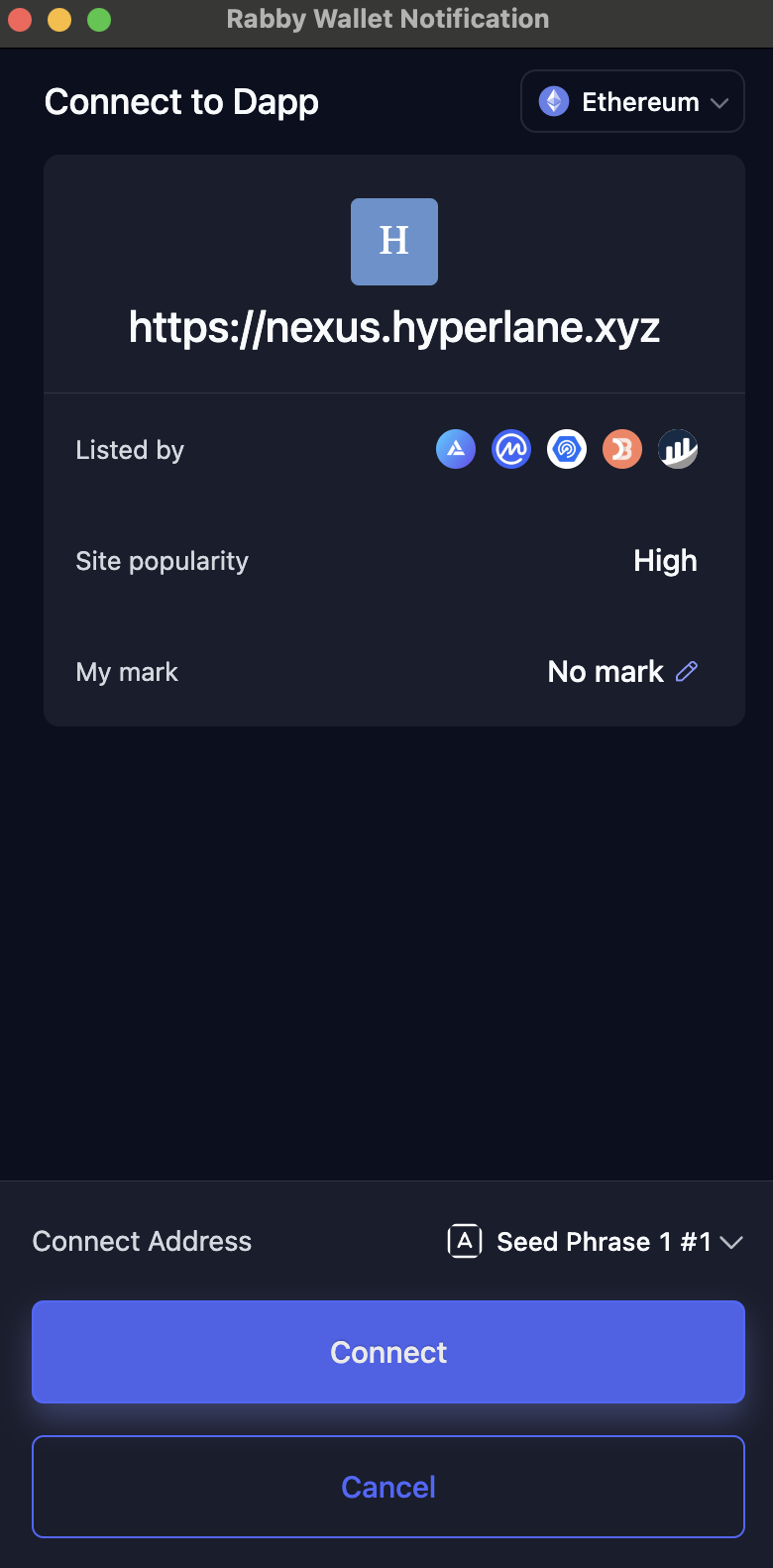
Wallets such as Rabby add another layer of security by surfacing trusted sources when connecting to a dApp. If a site is not recognized by established aggregators like CoinGecko or DeFiLlama, Rabby will flag the connection as high risk. This transforms wallet connections from blind trust into informed decisions.
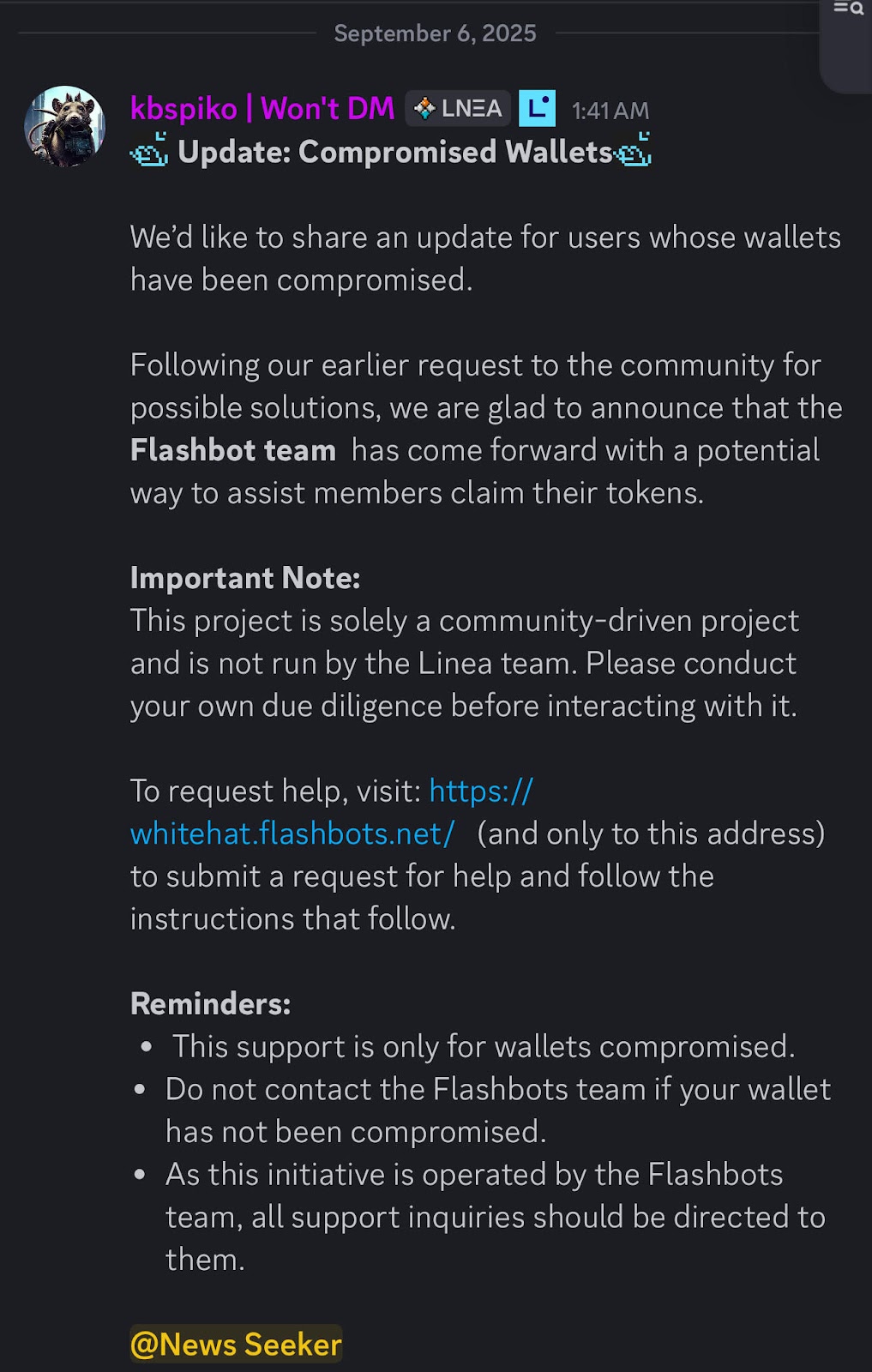
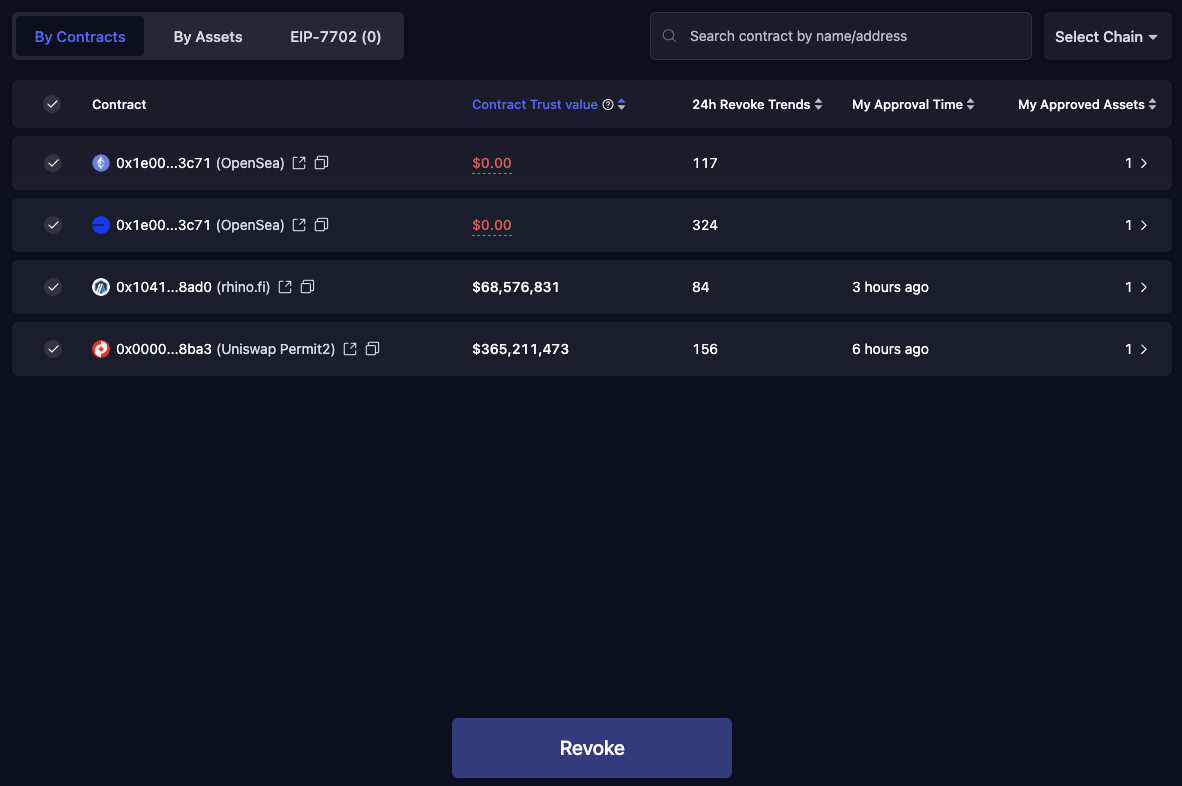
Approvals must also be actively managed. Tools like Revoke.cash allow users to monitor and revoke lingering permissions that could otherwise be exploited weeks or months later. For compromised wallets, whitehat-driven initiatives such as Flashbots have occasionally rescued funds by privately routing transactions before sweeper bots can front-run them. Yet even here, success is inconsistent. Prevention is always more reliable than recovery.
Browser hygiene remains critical. Unused extensions should be deleted outright, and updates applied promptly to eliminate vulnerabilities that can be exploited silently.
The principle is simple: every interaction with a wallet is a potential attack surface. Clicking a link, connecting to a site, authorizing an app, or approving a transaction can all open the door to attackers. Tools exist to reduce these risks, but their value depends on consistent and disciplined use. Security is not a one-time decision but a continuous practice.
Custody Illusions: The Centralized Exchange Trap
Centralized exchanges are a convenience, not a solution. They provide liquidity and fiat rails, but every deposit is an unsecured liability on their balance sheet. The hard truth is simple: if you do not control the keys, you do not control the coins.
Recent events have shown how quickly access can vanish. In August 2025, MEXC froze a trader's $3.1 million and demanded in-person KYC in Malaysia, a requirement never disclosed in their Terms of Service. Bybit halted withdrawals earlier this year under the vague banner of "compliance review," leaving users stranded for days with no clarity on whether the issue was regulatory, operational, or solvency-related. FTX remains the archetype: billions in customer deposits siphoned to cover hidden losses until the exchange collapsed outright.
The rule is absolute. Exchanges are liquidity venues for temporary balances, not vaults for long-term holdings. Proof-of-reserves dashboards cannot change this fact. The only reliable safeguard is cold storage in a hardware wallet, where control rests with the user and cannot be revoked overnight.
Physical Vectors: From $5 Wrench to Kidnapping

Digital wealth does not stay digital. Every transaction on-chain is traceable, and once a wallet is linked to a real identity, it becomes a target. The consequences are no longer theoretical.
In Brazil, armed criminals invaded a family's home and held them at gunpoint until multisig approvals were signed. In Mexico, traders were abducted and driven to remote locations, forced to transfer assets under threat of violence. In Eastern Europe, victims were beaten until they revealed seed phrases written down in their homes. Reports state that crypto-linked kidnappings and extortion have risen by more than 30% year over year, and the numbers continue to climb.
What makes this category uniquely terrifying is that there is no undo button. A stolen seed can cost you money; a targeted abduction can cost you your life. The mistake that puts you at risk is often simple: flaunting wealth online, doxxing your own wallets, or allowing personal information to leak through careless oversharing.
Prevention in the physical domain demands a different discipline. Seed phrases must never be kept at home. They should be etched into steel, encrypted, and placed in off-site vaults beyond reach. Decoy wallets with smaller balances can serve as sacrificial offerings if coerced. Most importantly, wealth should never be broadcast publicly. Flexing screenshots, boasting about holdings, or revealing identifiable details creates a trail that adversaries can follow.
In high-risk jurisdictions, situational awareness and physical preparedness are not optional. Security online is meaningless if you leave yourself exposed offline.
The Tooling Layer: Defensive Infrastructure
Security in crypto is strongest when it is continuous. Tools are most effective not as isolated apps but as overlapping layers that monitor, flag, and contain risk at different points of the transaction lifecycle.
Revoke.cash exemplifies this. Beyond one-off revocations, it provides ongoing visibility into the permissions a wallet has granted across protocols. Old approvals are often forgotten, but attackers do not forget. A single overlooked "setApprovalForAll" call can be weaponized months later. By surfacing these permissions in a single dashboard, Revoke.cash allows users to revoke unnecessary access before it becomes a live exploit.
Pocket Universe, ScamSniffer, and DeFiLlama's extension push security earlier in the chain. They do not just analyze transactions at the point of signing but act as continuous filters. Malicious links are flagged directly inside Twitter or Telegram. Scam domains are intercepted before they load in a browser. Explorer overlays mark suspicious addresses and tag known attacker wallets. This transforms defense from a reactive posture into an anticipatory one.
At the core sit hardware wallets. Devices such as Ledger, Trezor, Keystone, and GridPlus physically isolate private keys from web environments, reducing the risk of compromise to the physical realm. They must be paired with disciplined key management. A seed phrase should never exist online, in a screenshot, or inside a cloud backup. The only secure methods are pen-and-paper or etched steel, stored in an off-site location like a safety-deposit box.
The defensive stack is not about silver bullets. Each tool blocks a narrow set of attack vectors, but in combination they form overlapping safeguards that make exploitation harder and costlier. Yet tools themselves do not guarantee safety. They are only as effective as the discipline of the person using them. In crypto, security is not a feature to be toggled but a practice to be lived.
Further Resources
Defense is not only a matter of tools but of intelligence. The most resilient practitioners understand that vigilance is collective. A handful of independent researchers and firms have become indispensable for tracking threats in real time.ZachXBT remains the archetype of the on-chain investigator, tracing stolen funds across mixers and exposing fraud with forensic precision. Tayvano has emerged as a leading authority on wallet approvals and transaction hygiene, turning obscure mechanics into practical guidance. Officer CIA publishes deep security analysis and tactical briefings, with his archive on Mirror serving as a living library for the community. Zun provides whitehat rescue services when wallets are compromised, coordinating private transactions to outpace sweeper bots. Flashbots, through its whitehat portal, extends that infrastructure to anyone facing imminent loss.
Institutional actors also warrant attention. CertiK monitors exploits at scale, publishing alerts and postmortems that often serve as the first signal of systemic risk. Lookonchain specializes in real-time wallet forensics, identifying suspicious flows long before they reach headlines. Arkham Intelligence provides granular entity tracking and visualization tools, mapping stolen funds and linking wallets to known actors. Together, they form an early warning system that no individual could replicate alone.
Education is equally critical. Platforms like Unphishable.io simulate common web3 scenarios, conditioning users to recognize red flags before they encounter them in the wild. The principle is simple: security is not static. By embedding yourself within the flow of information from these investigators and institutions, you inherit the vigilance of an entire community.
Cryptonary's Take
Security failures now overshadow market swings as the greatest threat to portfolios in 2025. Billions have already been stolen this year through social engineering, technical exploits, and custody failures. The Lazarus Group's $1.5 billion theft from Bybit, the hijacking of Yuga Labs' official accounts, and the breach of Ledger's GitHub repository all prove one point. If institutions, protocols, and veteran teams can be targeted, so can every individual user.Every wallet without proper custody is already exposed. Attackers do not wait for permission, they wait for mistakes. And in crypto, a single mistake is final.
The only effective response is uncompromising self-custody. Hardware wallets are not optional. They are the foundation that keeps your assets beyond the reach of scammers, malware, and compromised exchanges. Ledger has established itself as the industry standard because it transforms security from an afterthought into a safeguard.
The message is simple. Remove funds from exchanges. Store your seed phrase offline and off-grid. Secure your holdings with a Ledger before your portfolio becomes the next headline.
Get a Ledger HERE.







